Computer Networking
 The internet—together with all of the applications it supports, like the web—has become one of the most important forces for technological progress of our era.
The internet—together with all of the applications it supports, like the web—has become one of the most important forces for technological progress of our era.
In this course we’ll cover the key protocols that enable the internet, the web, and other applications of computer networking. This should empower you not only to make the most of present networking technologies but also to help build the future.
At the core of this course are the sequences of problems for each topic. You should aim to solve each problem, using the worked solutions and supplementary explainers as needed. There are also some full seminars, which some find helpful to tie topics together. While no textbook is necessary for this course, we do recommend Computer Networking: A Top-Down Approach (“Kurose & Ross”) as a supplement, and reference relevant Kurose & Ross chapters below. For more suggestions on how to approach CS Primer, see the how-to guide.
Introduction to network programming
This first module covers the basics of network protocols, and network programming using sockets. It also presents the layered model of network protocols and the idea of encapsulation.Due to the layered model, application layer protocols like DNS, HTTP, and SMTP can be built in isolation from concerns like routing and reliable delivery. Similarly, TCP can focus on transmission and IP can focus on routing without having to consider the application data. We use a simplified 5-layer version of the OSI 7-layer networking model, as does Kurose & Ross. See OSI: The Internet That Wasn't for a sense of why the OSI model itself doesn't quite match reality.
For those using Kurose & Ross, supplementary material is available in chapter 1: "Introduction". For a popular introduction to socket programming, see Beej's Guide to Network Programming.
If you're unfamiliar with binary encodings of data, we highly suggest first working through at least a few problems of the "Bits and bytes" module of Computer Systems.
Problems
| Shout server FREE | implement a shouty echo server to learn socket basics (14:14) |
| HTTP header server | write a small HTTP server to learn about the listen and accept syscalls (27:06) |
| Simple DNS client | you'll write one! (50:42) |
Seminars
Explainers
Application layer: HTTP in depth
There are 1000s of application layer protocols; they are common enough that you may one day develop one yourself.Consider that in April 2001, Bram Cohen quit his job and started designing what would become BitTorrent. He released the first implementation 2 months later.
Of those, the World Wide Web is by far the best known, and the only one at risk of being confused with the Internet itself. It is really the "killer app" of the Internet, and its underlying protocol HTTP is now employed well beyond its original purpose of delivering HTML pages to browsers.Sir Tim Berners-Lee conceived of and first prototyped the Web—including its key protocols HTTP and HTML—in 1989, a full two decades after ARPANET was conceived. Pictured below is Berners-Lee at CERN in 1994, demonstrating web pages.

Given the ubiquity of the web, we will dedicate particular attention to digging into some of the details of the HTTP. We will do this by building a proxy server—like a simplified nginx—capable of caching and load balancing. Given that many of the interesting aspects of web infrastructure engineering comes from the nitty gritty of having these systems run at high throughput, we will pay at least some attention to resource management and performance.
Along the way we'll also discuss the evolution of HTTP including the most important differences between HTTP/1.1 and HTTP/2.HTTP/3 is really just HTTP over QUIC, which solves a set of typically transport layer responsibilities. We will return to it once we've covered TCP.
For those following Kurose & Ross, we suggest the section "Web and HTTP" of chapter 2.
Problems
| HTTP proxy: basic proxying | use socket system calls to implement a basic HTTP proxy (50:54) |
| HTTP proxy: persistent connections | write an HTTP parser and extend the proxy to support persistent connections (1:33:24) |
| HTTP proxy: concurrency | use non-blocking sockets and I/O multiplexing for concurrency (1:19:53) |
| HTTP proxy: features | add gziping, caching and other functionality to your proxy (1:15:21) |
Explainers
Application layer: DNS in depth
Many are surprised to learn that DNS is an application layer protocol, and that to resolve a URL into an IP address we must make a network request to a DNS server (identified by its IP address!).DNS was first designed in 1983. Astonishingly, until its deployment, the mapping between names and addresses was maintained in a simple text file HOSTS.TXT on a server at SRI International (previously Stanford Research Institute) from which every host on the network downloaded a copy! Here is the HOSTS.TXT file from early 1983.
For those following Kurose & Ross, we suggest the section "DNS—The Internet's Directory Service".
Problems
| DNS client: message compression | understand what exactly a domain name is, by implementing compression (38:33) |
| DNS client: reverse DNS | Extend your DNS client to support reverse DNS lookups (18:08) |
| DNS client: more record types | Support further record types to appreciate the versatility of DNS (1:09:18) |
| DNS client: tracing resolution | Fully resolve DNS queries from the root servers down (1:07:37) |
Explainers
Transport layer: TCP and QUIC
This module covers the critically important transport layer, and its two major protocols TCP and UDP. We will consider the challenges involved in guaranteeing delivery over an unreliable network, and the implications of how TCP achieves this and its other features such as segmentation. Once we have a good understanding of the trade offs made by TCP, we will have gained an appreciation for when we may wish to ignore TCP entirely and just use UDP instead!UDP is in essence “not using TCP”. David P. Reed is often considered the “designer” of UDP, which he finds embarrassing, as he sees it as a simple matter of factoring out of TCP/IP.
We also explore QUIC, a new alternative to TCP filing a similar role but over UDP, and providing the transport functionality for HTTP/3.
For supplementary material, we suggest the Kurose & Ross chapter on the Transport Layer, as well as the video: QUIC: next generation multiplexed transport over UDP.
Problems
| Lossy download | stitch an image back together from the raw packets captured on a lossy network (39:24) |
| Reliable transport | design and implement a simple reliable transport protocol (1:27:02) |
| Reliable transport: sliding window | improve the throughput of your protocol with flow control |
| Reliable transport: multiple streams | implement a QUIC-like multi-stream realiable transport |
Explainers
You can’t gaze in the crystal ball and see the future. What the Internet is going to be in the future is what society makes it. Bob Kahn, co-creator of TCP/IP Network layer: IP and ICMP
This module covers the protocols required to route packets correctly through the internet, and provides a glimpse into the structure of the internet as a collection of "autonomous systems".
We also undertake a major programming exercise: to develop a version of traceroute that's better than the original. This provides a good opportunity to think about concurrency, and to better understand some of the protocols we've encountered to date.
For supplementary reading, we suggest the Kurose & Ross chapter on the Network Layer.
Problems
| Traceroute | learn about IP routing and raw sockets, by writing a traceroute clone (1:03:48) |
| Traceroute: autonomous systems | extend your traceroute clone to show autonomous systems (45:39) |
| Traceroute: ICMP probes | replace your UDP probe with ICMP, and write the checksum function (30:54) |
| Traceroute: customization | improve concurrency or add further features to your implementation (1:09:06) |
Explainers
Network security
Security was not a first class concern of the pioneers of computer networking,Consider that many of the core ideas of TCP were decided upon in 1973, when there were only a few dozen nodes on ARPANET, most of them universities. Pictured below is a map of the network at the time.
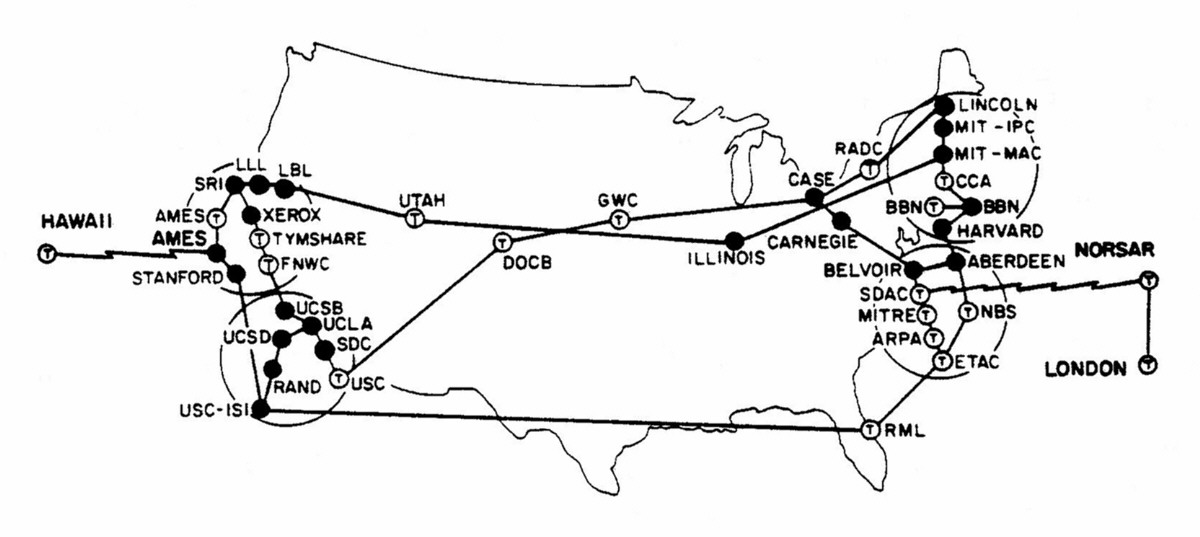 and so is not at the core of its most important protocols so much as retrofitted around them. With time and the increasing popularity of networked applications, it’s become clear that security is now a critically important consideration.
and so is not at the core of its most important protocols so much as retrofitted around them. With time and the increasing popularity of networked applications, it’s become clear that security is now a critically important consideration.
This module covers the means by which we can secure Internet communication, with a particular focus on public key encryption, SSL/TLS, and the role of certificate authorities. A tremendous amount of work has been invested in these schemes, with the remarkable result that we can now send data securely over a network that we know to be untrustworthy.
For supplementary reading, we suggest the Kurose & Ross chapter on security.
Expected release: late 2023